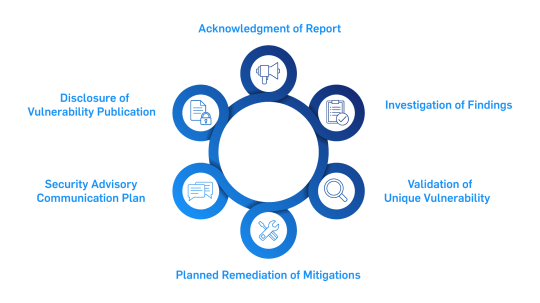
If you believe you have discovered a security issue within any Carrier offering, please send an email to [email protected] with the following information to help us better understand the nature and scope of your finding:
- Product Name
- Software / Firmware / Hardware Version
- Description of Issue / Concern
- Reproduction Steps
- Contact Information